Following our previous article on solving the challenge of modern Governance Risk and Compliance (GRC), it’s now time to discuss the step for modern businesses to bring in the critically important Information Security Management System (ISMS).
Technology and security practitioners have often been working in isolation, away from their GRC cousins. As a result, gaps in language and understanding of risks have grown. Many organisations continue to struggle to find ways to unify technical/security speak with and the language of business. Also, the GRC world can often be an ideal paradise and not ‘in sync’ with the real technology and security picture.
-
Why do you need an Information Security Management System (ISMS)?
-
The advantage of using 6clicks as your ISMS Solution
-
How do GRC and ISMS practices compare?
-
Getting Started with an ISMS Framework: 4 Simple Steps
-
What is an ISMS?
-
What are the benefits of an ISMS?
6clicks: the software & content that will bring it all together!
What is the need for Information Security Management System (ISMS) implementation?
An Information Security Management System (ISMS) based on ISO/IEC 27001 will enable you to manage information security-related risk, hopefully, improve your security maturity, and demonstrate compliance to both internal and external compliance requirements. All this should give your organisation confidence, build trust and help you achieve your objectives.
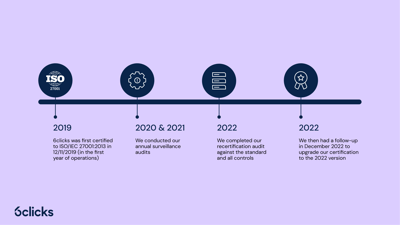
ISO 27001 is considered the ‘gold standard’ when it comes to information security for good reason. Demonstrating a complete ISMS is a core requirement for achieving one’s ISO 27001 certification. Currently, the industry's ‘best’ practice ISMS is largely dictated by international standards that cover both ISMS and control requirements.
For our GRC friends, ISO 27002 offers a guide for codes of practice to drive the enforcement of the specification found in ISO 27001 and its Annex A.
6clicks already has ISO/IEC 27001 mandatory requirements and Annex A controls in the 6clicks Marketplace so you can easily perform assessments. We have also released a suite of information security control sets and policies specifying essential roles and responsibilities. Simply make sure you assign someone in your organisation to the relevant roles and you’re good to go! Welcome to the world of a turn-key ISMS.
The trick is to iterate through the process of assessing and remediating on a regular basis to refine your security program and achieve continuous improvement in a similar way to agile software development practices are carried out. This is a far superior option than waiting for some form of annual audit or falling short, suffering incidents and implementing security reactively.
We have some bonus capabilities that go beyond GRC and that start with asset management; the ability to identify and classify information assets using a customisable schema. You can then link risk assessments to impacted assets and understand what is at risk. This is a capability that we plan on expanding to include threat and vulnerability-related information.
With 6clicks, you’ll identify what you need to do faster and create more time to implement the requirements rather than spend too much time preparing spreadsheets and long documents. If you have the capacity internally you can tailor everything yourself. Or you may choose to work with one of our cyber and information security-focused service provider partners. Either way, you come out the other side a winner!
6clicks provides a platform that unifies traditional GRC with IT and information security management practices, so they can work together more effectively. A single platform addresses both sets of requirements that translates between often siloed information. Finally, 6clicks helps to connect GRC with real data from the IT and information security worlds.
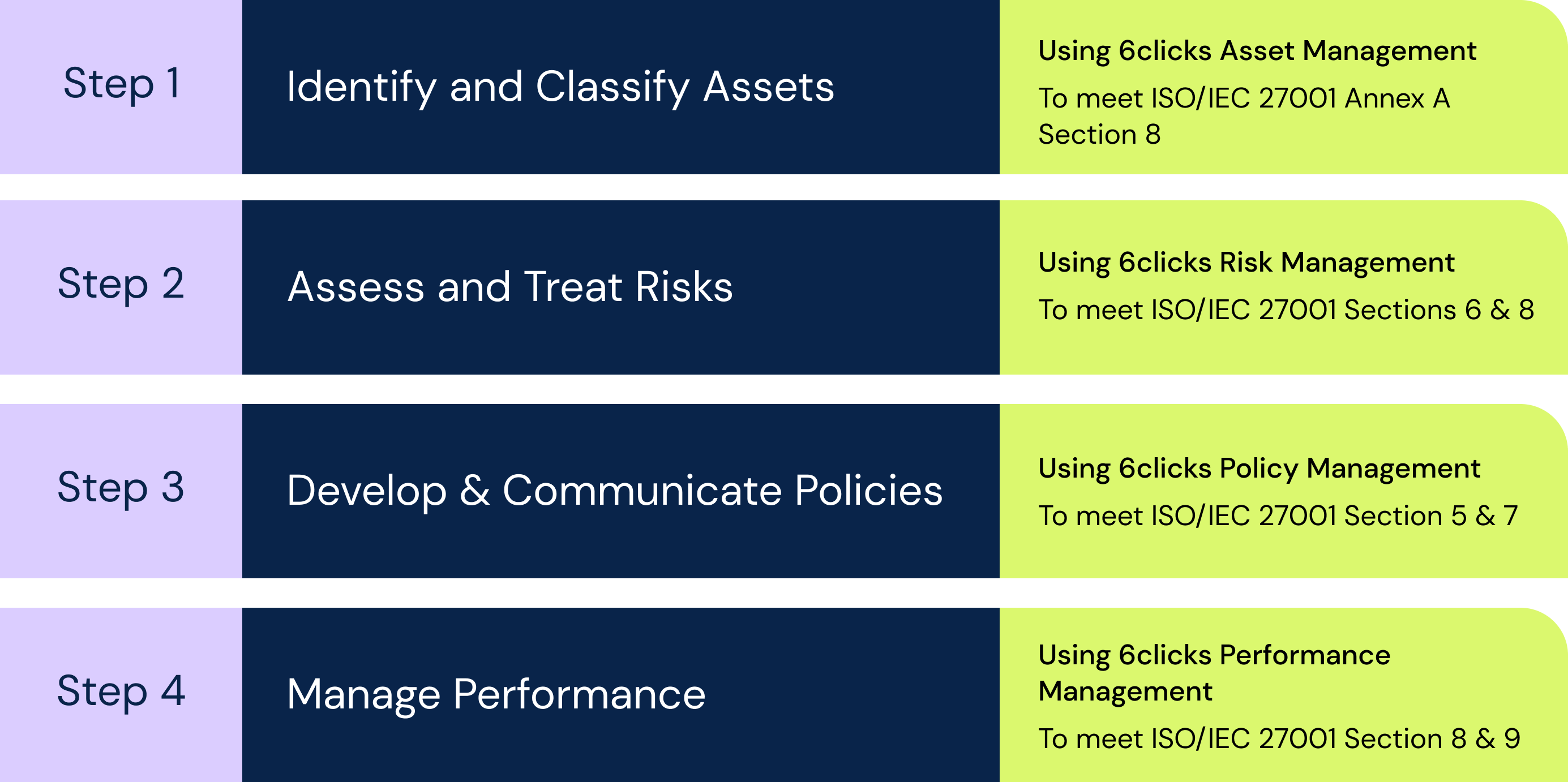
Step 1. Identify and Classify Assets
The first step in applying security and establishing an ISMS is to understand what you need to protect. To do this consider your business activities and processes, and the information that is required as an input or results as an output. To meet the requirements of ISO/IEC 27001 Annex A Section 8, you then need to assign an owner and a security classification.
The 6clicks Asset Management capability lets you record your information assets including owners, relevant third parties (that have access or host the information asset), and security classification. The security classification scheme is fully customisable to suit whatever values you prefer. You can then link your risks to the impacted assets, so you know what is at risk (and who is responsible for it).
Step 2. Assess and Treat Risks
The second step in applying security and establishing and ISMS is to assess and treat risks. To get this step started, you will need to identify cyber and information security related risks which can be achieved by forecasting the scenarios that may impact your organisation’s achievement of its objectives such as ransomware, privacy breach or service disruption.
You can use 6clicks Risk Review for Teams (available now on iOS) to identify and assess risks that will then populate the 6clicks Risk Management capability. Within the 6clicks web app you are able to add references to existing controls (and compliance requirements), perform assessments of likelihood and impact, and manage risk treatment plans (drawing from external control libraries or your internal control framework).
Step 3. Develop & Communicate Policies
The third step in applying security and establishing an ISMS is to develop and communicate policies. Rather than ramble on in long winded documents that are printed, put into a binder and sat on the shelf, policies should be succinct responsibility statements that are assigned to specific people or roles in your organisation. And if they are critical, they should be continuously measured and improved.
The 6clicks Policy Management capability enables you to define an internal control framework, mapped to any number of external compliance requirements, and any number of responsibilities with optional performance checks. You can then enable the people in your organisation to see the responsibilities that relate to their role (rather than bury them in binders).
Step 4. Manage performance
The final step in applying security and establishing an ISMS, perhaps the most critical step, is to manage ongoing performance. You need to identify and record details when things don’t go to plan, so you can update your plans and try to prevent recurrence where possible. Speeding up the cycle between planning, implementing and measuring will allow you adapt and improve faster.
The 6clicks Performance Management capability enables you to schedule regular checks of critical controls and activities when defining policies. People within your organisation can then input the results of such checks so you can determine whether controls are operating effectively or not. You can also perform internal and third-party assessments.
An Information Security Management System is the cornerstone of effective risk management for any organisation, and here’s why.
Effective risk management is not just the purview of those responsible for GRC, but for all team members – at least on some level. While this can be a challenge to proactively maintain, protecting and monitoring your organisation’s information is where an ISMS can really prove it’s worth. And even more so when managed digitally.
Built on the three pillars of people, process and technology an ISMS will help you achieve compliance with a wide variety of standards, laws and regulations – including ISO/IEC 27001 certification requirements included in its Annex A control library, as well as privacy-specific legislation.
‘Information’ can mean a whole lot. So, let’s break down the features of information that need to be seriously considered:
- Purity: it is vital that your information holds integrity. In other words, your information is protected from corruption, is complete, and above all else, accurate.
- Accessibility: you must show that your information is available and usable to those that are authorised.
- Privacy: crucially, you must demonstrate that your confidential information is not accessible to external people, processes or other parties that are not authorised.
An ISMS framework that complies with ISO 27001 requirements does not just ‘tick a box’.
It also gives you all of these excellent advantages:
- Adaptability: It means you can make quick manoeuvres by responding to evolving security threats and changes both within your organisation and the outside environment. Say hello to threat reduction!
- Reduced costs: You can reduce your costs spent on adding layers of technology and practices that might not work. This is thanks to the risk assessment and analysis approach of an ISMS.
- Resilience: Curating and executing an ISMS can increase your company’s resilience to cyber attacks. As we say here at 6clicks, ‘compliance is not resilience’ (although it should be!).
- Centralisation: An effective ISMS (contact us to get this done) gives you a fantastic centralised framework for securing your information…and keeping it.
- Security-first company culture: Watch your company culture shift as the ISMS blankets your entire company, not just the IT department. Empower your staff to understand and tackle security issues within their respective domains. Let them embrace risk as part of their everyday attitude!
- Forms: Not ‘that’ kind of form (please god no!). Whether your information is paper-based, sitting on the cloud or various other digital existences, an effective ISMS helps you protect it all (electronic, hard-copy, verbal etc.).
- Protection: Remember the bit above when we talked about the ‘features’ of information? Well, an effective ISMS protects the intimate details of your information. The purity, accessibility and privacy of your information is supported by an ISMS by way of it’s policies, procedures and technical and physical controls.
And that’s all I have...
Well, not really. But if you want to chat with me about how 6clicks can help your business develop and maintain an ISMS, make sure to book some time with me - I have a limited amount of time available for bookings!




%20(1).png?width=320&height=650&name=Webinar%20Template%201%20(320x650px)%20(1).png)